This is a list of posts with tags Tutorial
Guide to Using CherryTree on Kali Linux
CherryTree is a hierarchical note-taking application used by many cybersecurity professionals, including Kali Linux users. As a highly flexible tool, CherryTree …
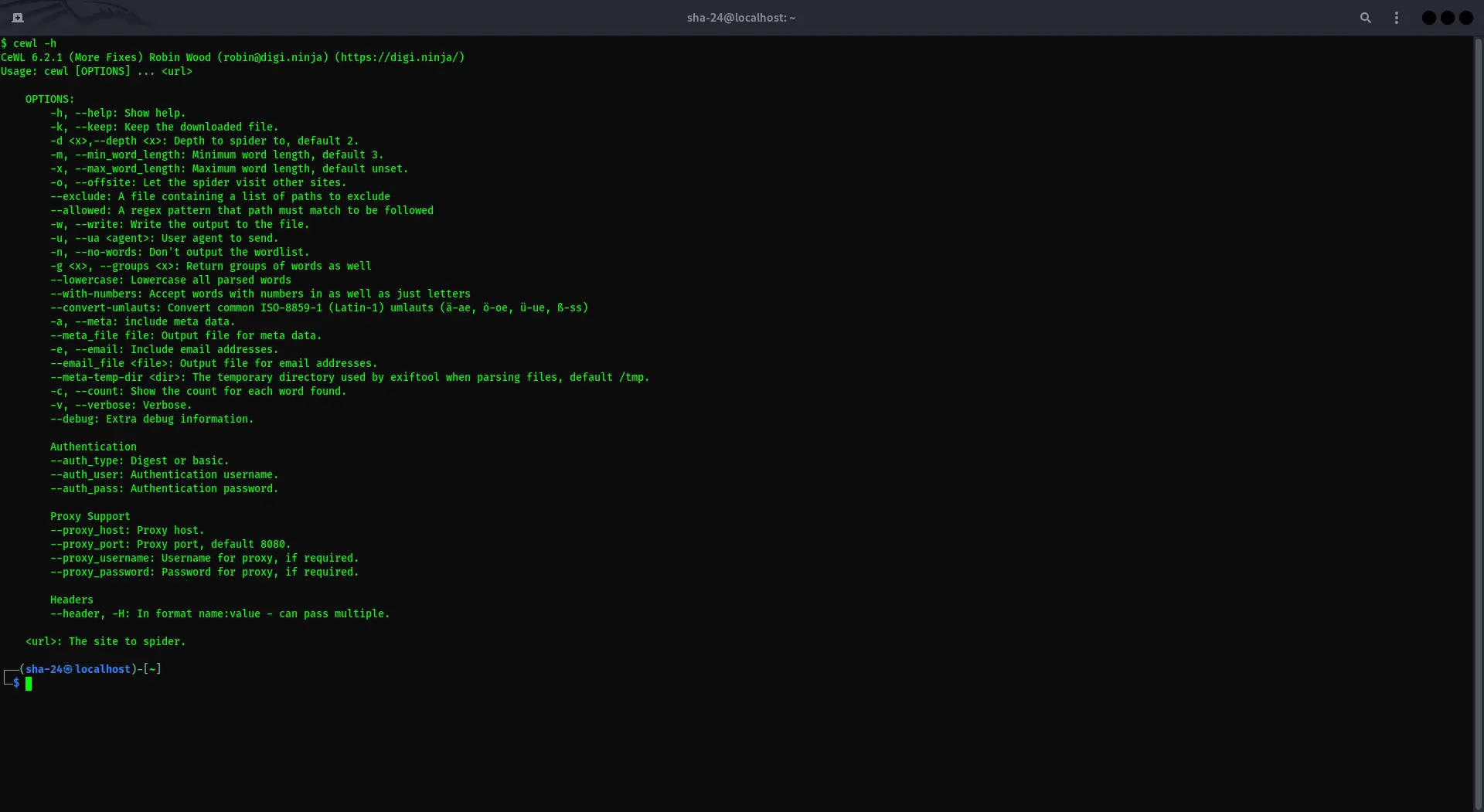
CEWL on Kali Linux: A Complete Guide to Using Custom Word List Generator
Kali Linux is a popular Linux distribution designed specifically for pentesting and cybersecurity purposes. One of the tools available in this distribution is …
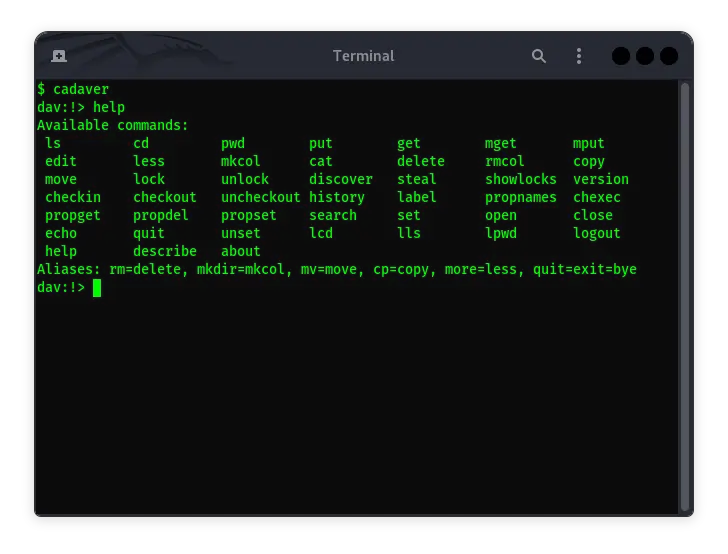
Cadaver in Kali Linux: Usage Guide and Features
Cadaver is one of the command-line based tools used to interact with WebDAV (Web Distributed Authoring and Versioning) servers. WebDAV allows users to manage …
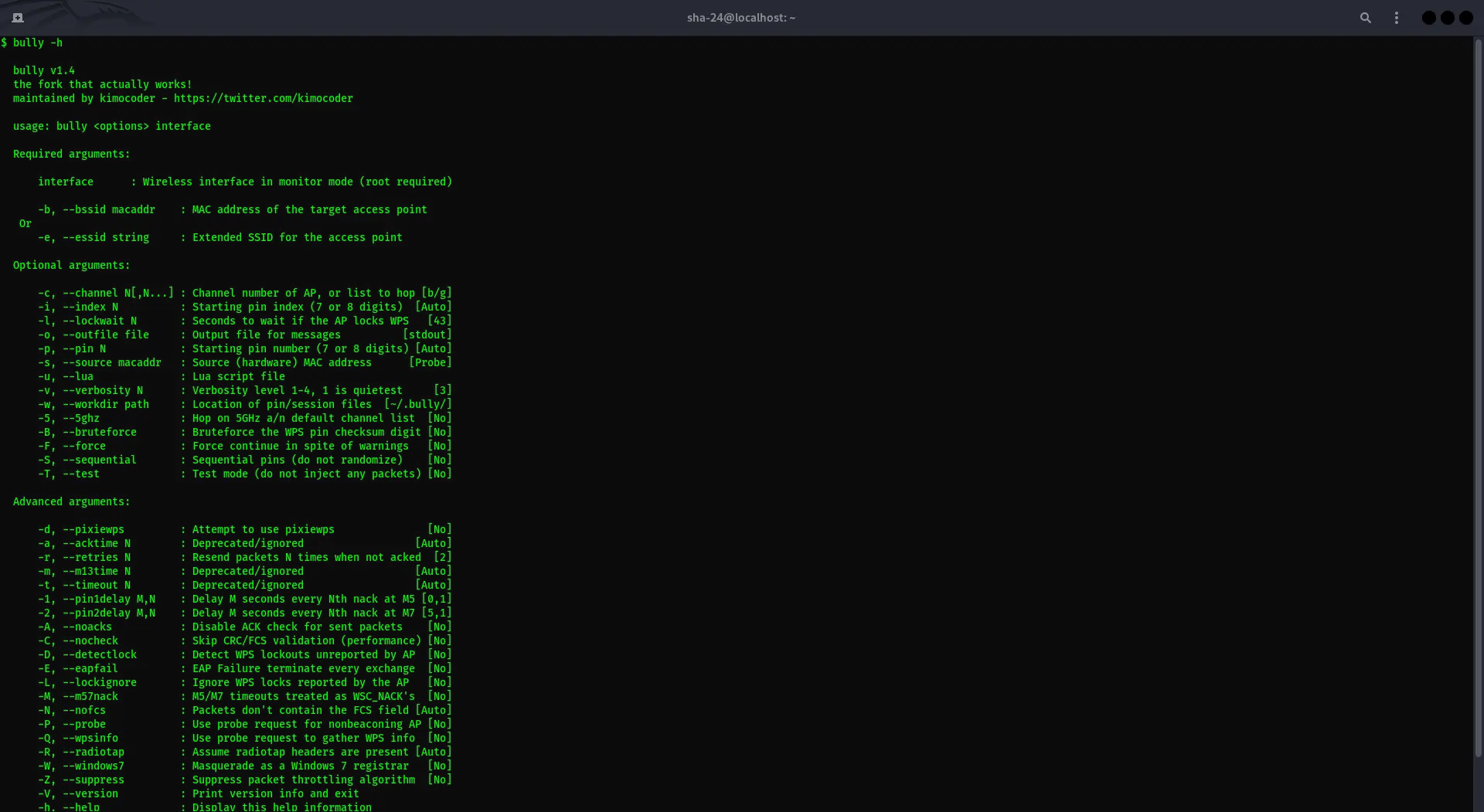
Bully Cracking in Kali Linux: A Tool That Can Crack Wi-Fi Passwords
Kali Linux has long been known as a specialized operating system for penetration testing and cybersecurity. One tool that often gets attention is Bully, an …
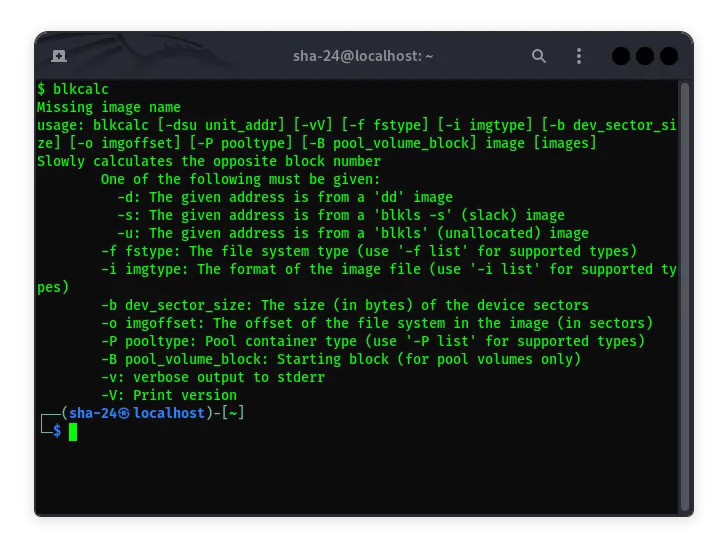
Getting to Know blkcalc in Kali Linux: A Complete Guide
Kali Linux is a Linux-based operating system distribution specifically designed for digital forensics and security testing. One of the essential tools available …

How to Use Binwalk on Kali Linux for Firmware Analysis
Binwalk is one of the tools often used in the world of cybersecurity to perform firmware analysis. Binwalk is used to extract files contained in firmware, be it …