This is a list of posts with tags Exploit

What is an XSS Attack? And How to Deal with It?
In the world of web security, Cross-Site Scripting (XSS) is one of the most common and potentially damaging types of attacks. XSS is a type of attack in which …
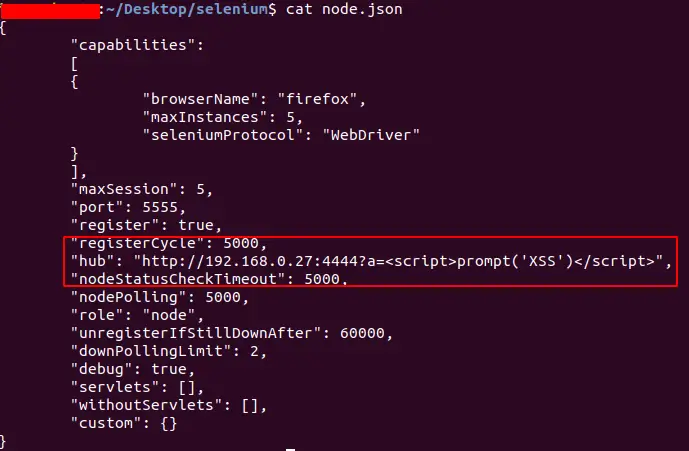
XSS Payload: Understanding, Risks, and Examples
Cross-Site Scripting (XSS) is one of the most common types of cyber attacks on web applications. XSS allows attackers to inject malicious scripts into a web …

WPScan: Identify and Secure WordPress from Vulnerabilities
WordPress has become one of the most popular platforms for building websites worldwide. From personal blogs to large e-commerce sites, WordPress offers …

Understanding Solara Exploit: Definition, Impact, and Prevention Steps
Solara Exploit is a term that has emerged in the world of cybersecurity lately. This exploit refers to a series of security holes that are attacked through …

Recognizing and Preventing Exploits in Laravel
Laravel is one of the most popular PHP frameworks in the world, especially among web developers because of its ease of use, good performance, and the security …

Winbox Exploit on Mikrotik: How it Works, Risks, and Prevention
Winbox is a GUI (Graphical User Interface) application designed by MikroTik to allow users to easily configure MikroTik router devices. This application is very …