This is a list of posts with tags Cyber Security

Popular Cloud Storage: The Best Choice for Your Storage Needs
In today’s digital era, the need for reliable and flexible data storage is increasingly important. Cloud storage has become a popular solution due to its …

How to Become a Professional Bug Hunter
Becoming a professional bug hunter requires a deep understanding of computer and network security. Understand how operating systems, web applications, and …

How to Use Hashcat Kali Linux
Hashcat is a popular tool widely used for password cracking, and is relied upon by cybersecurity professionals to test password vulnerabilities. Hashcat …
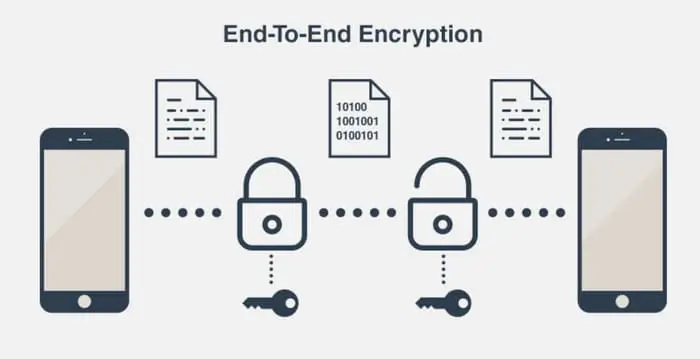
How to Enable and Disable End to End Whatsapp
End-to-end encryption is a security feature that ensures that only you and the recipient of the message can read the messages sent. WhatsApp uses end-to-end …

How to Update Personal Information
Cybersecurity is of utmost importance in today’s digital world. With the increasing number of cyber threats, it is important to ensure that your personal …

How to Detect Phishing Attacks?
Detecting a phishing attack requires vigilance and knowledge of the signs commonly used by attackers. Here are some ways to detect a phishing attack: