This is a list of posts with tags Cyber Security

SQL Injection: Definition, Dangers, and How to Prevent It
SQL Injection is an attack technique that exploits vulnerabilities in SQL (Structured Query Language) based applications. With this attack, an attacker can …

What Is Spear Phishing? Definition, How It Works, and How to Protect Yourself
Spear phishing is a form of cyberattack that targets a specific individual or organization in a very specific and planned way. Unlike regular phishing, which is …

What Is a Firewall and Why Is It Important for Network Security?
Firewall is an important component in a network security system that functions as a barrier between internal and external networks, such as the internet. Its …

Email Spoofing: What It Is, How It Works, and How to Avoid It
In today’s digital era, email has become a very important communication tool. However, with the increasing use of email, the risk of cyber threats has …
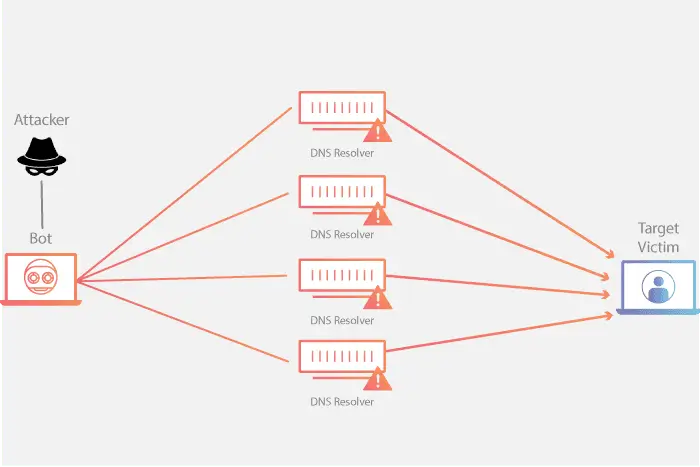
What Is DNS Amplification?
DNS Amplification is a type of Distributed Denial of Service (DDoS) attack that utilizes the Domain Name System (DNS) protocol to increase the amount of traffic …

What Is Delta Exploit?
Delta exploit is a term used in cybersecurity to refer to a type of exploit that takes advantage of a gap or vulnerability in software or a system. Delta …