New Post

Powerful Way to Get WiFi Handshake with Aircrack-ng
Syukra
In the world of cybersecurity, understanding how WiFi networks work and how to protect them is crucial. One of the most important processes in testing the …
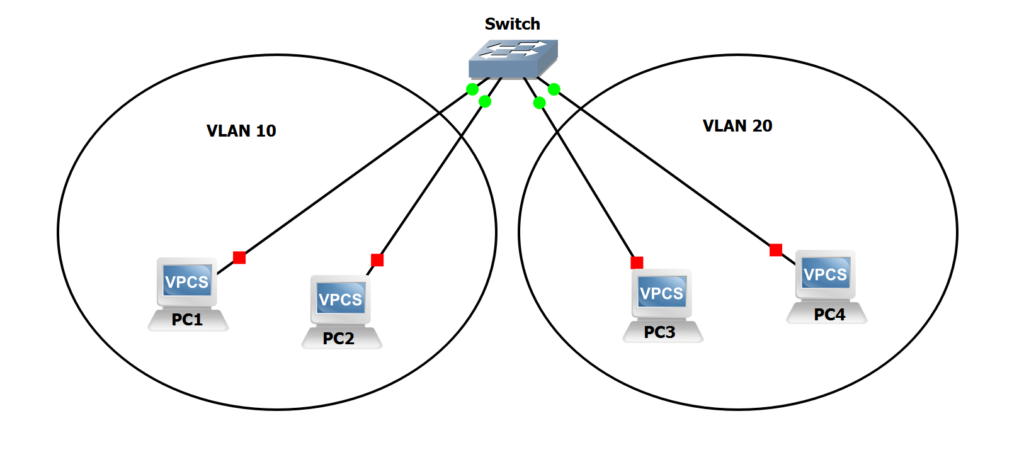
Get to Know VLAN: A Secure and Efficient Network Solution!
Syukra
Virtual Local Area Network (VLAN) is a networking technology that allows logical segmentation within a physical network. With VLAN, a single physical network …

Top 10 Cyber Security Companies in the World 2025
Syukra
In today’s digital era, cybersecurity is a top priority for companies, governments, and individuals. With cyberattacks increasing every year, the need for …
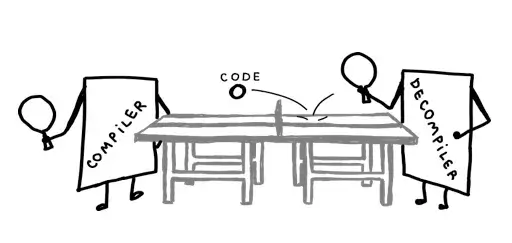
Compiler vs Decompiler: Differences You Must Know!
Syukra
In the world of programming, two terms that often appear are compiler and decompiler. Although they sound similar, both have very different functions and roles. …
Stuxnet: Advanced Malware That Changed the Digital World
Syukra
When discussing the most legendary cyber attacks in history, the name Stuxnet is never absent. This malware is not just an ordinary computer virus, but a cyber …

NestJS vs Next.js: A Complete Comparison for Modern App Development
Syukra
In the modern world of web development, various frameworks and technologies have emerged to make it easier for developers to build scalable, fast, and efficient …
