New Post

How Does Two Factor Authentication Work?
Syukra
Two-Factor Authentication (2FA) is a security method that requires two types of identifying information from a user to access an account or system. The purpose …

What Is the Difference Between Phishing and Malware?
Syukra
Phishing and malware are two common types of cybersecurity threats, but they have different characteristics and purposes. Here is an explanation of the …
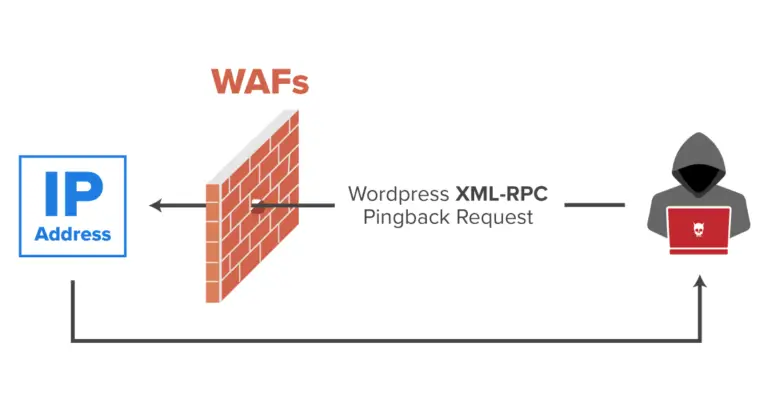
Getting to Know xmlrpc.php and Its Security Exploits
Syukra
In the world of cybersecurity, the xmlrpc.php file in WordPress is often targeted by attackers. xmlrpc.php is a default WordPress file that allows external …

What Is Tailgating?
Syukra
Tailgating is a term that is often used in a variety of contexts, but it generally refers to the act of following someone too closely. The concept is often …
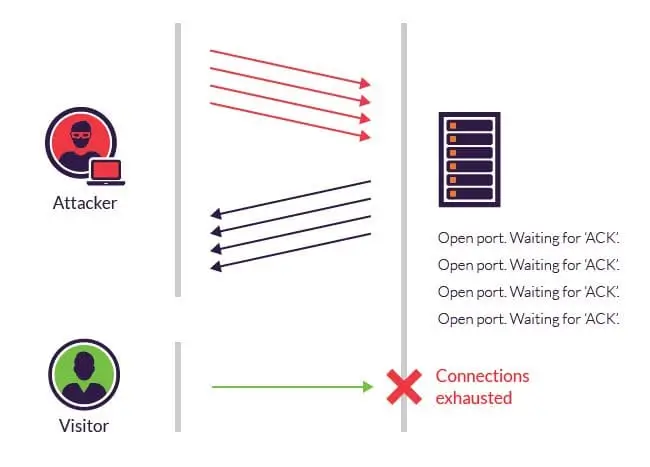
Understanding SYN Flood: A DDoS Attack That Disrupts Network Performance
Syukra
SYN Flood is a type of DDoS (Distributed Denial of Service) attack that targets the Transport layer of the OSI (Open System Interconnection) model. This attack …

SQL Injection: Definition, Dangers, and How to Prevent It
Syukra
SQL Injection is an attack technique that exploits vulnerabilities in SQL (Structured Query Language) based applications. With this attack, an attacker can …
