New Post

Most Dangerous Types of Malware Viruses
Syukra
In today’s digital world, viruses and malware are a real and serious threat to internet users. Here are some of the most dangerous types of viruses and …
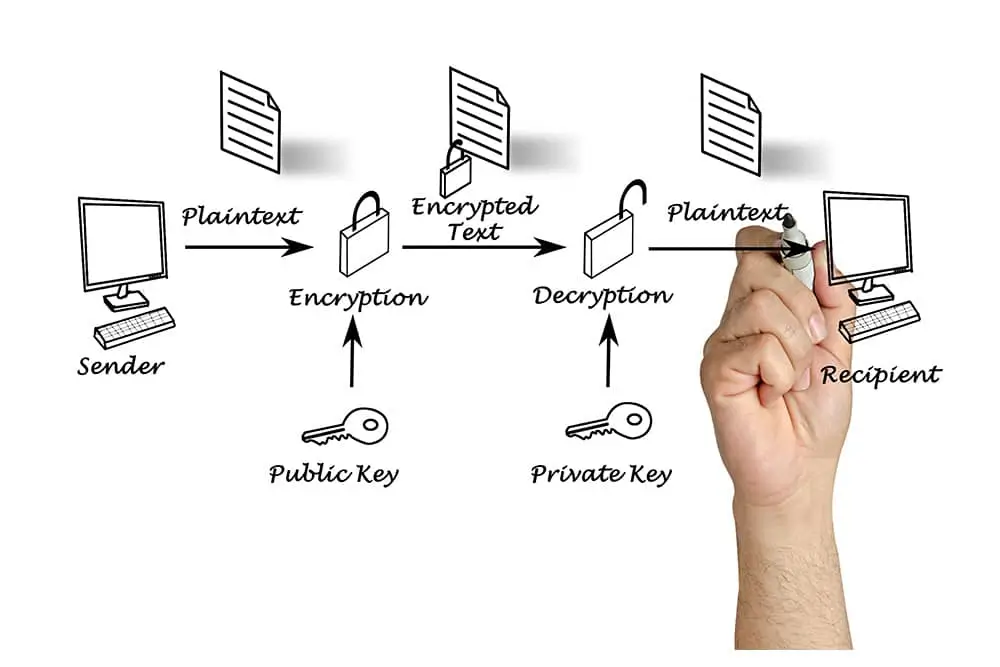
Types of Security Encryption: Definition, How It Works, and Examples
Syukra
Encryption is a data security technique that aims to protect information so that it can only be accessed by authorized parties. In today’s digital world, …

Best Antivirus Types Today
Syukra
In the increasingly advanced digital era, it is important for us to protect our devices from cyber threats. Antivirus is a crucial tool in keeping our personal …
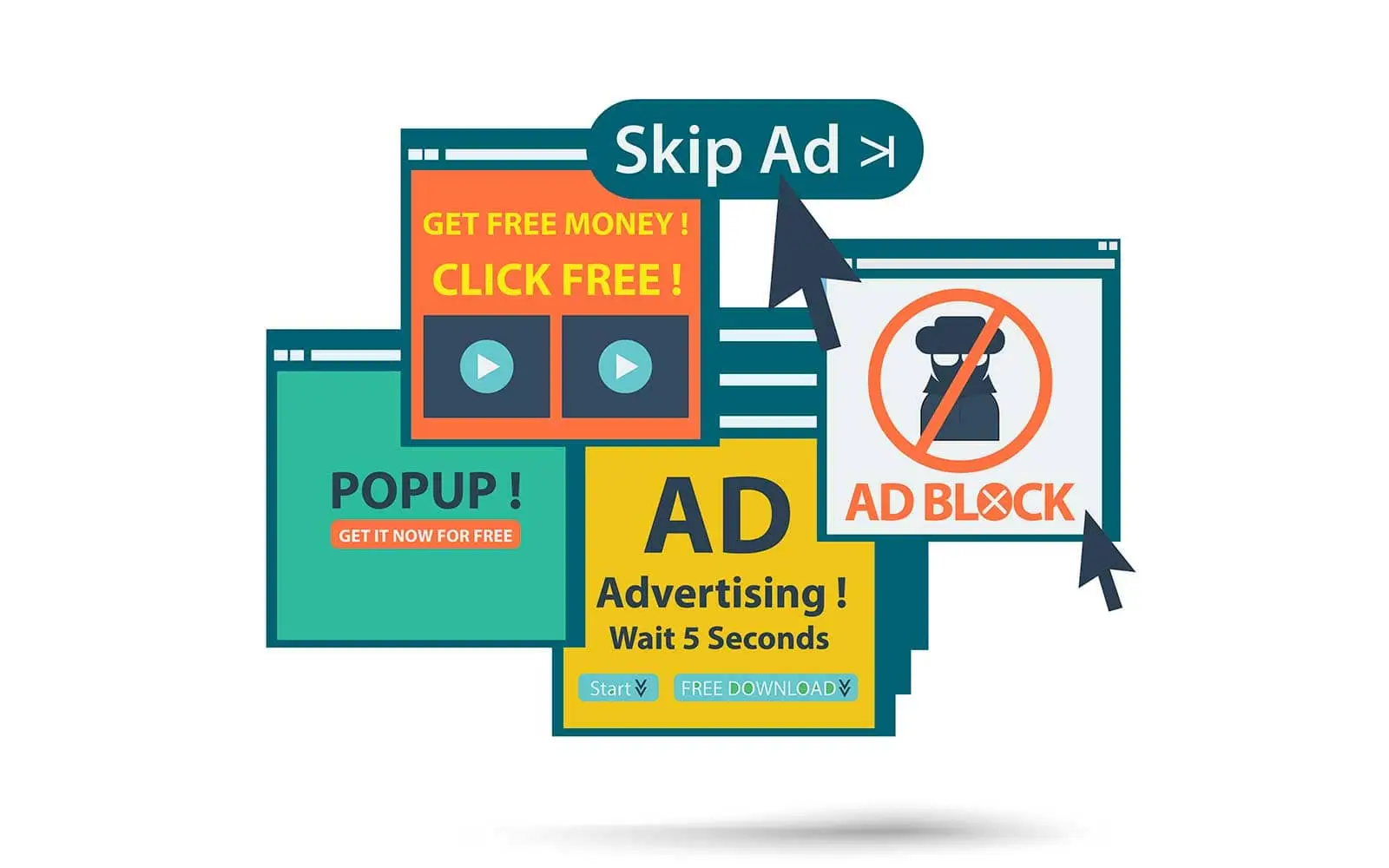
What Are The Most Dangerous Types Of Adware?
Syukra
Adware is software that displays unwanted advertisements to users. While some types of adware are considered less dangerous, there are certain types of adware …

Infinite Loop in Programming
Syukra
In programming, an infinite loop is a construct in which a particular block of code is executed repeatedly without stopping. Often, the exit condition for the …

Cybersecurity Salary in Indonesia
Syukra
In today’s digital era, the need for professionals in the field of cyber security is increasing. Every year, many companies are turning to digital …
