New Post
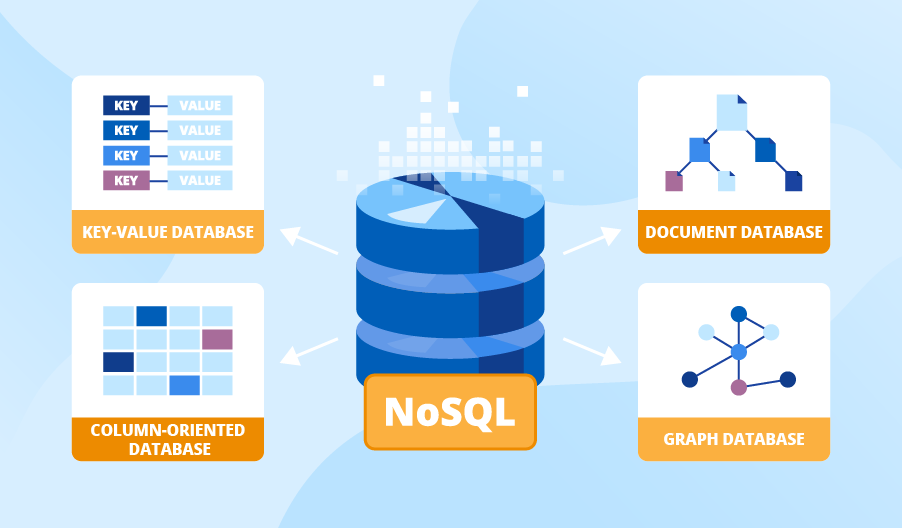
Understanding NoSQL Databases: Definition, Types, and Advantages
Syukra
Along with the increasing need to handle increasingly complex and large data, new data storage solutions have emerged that can overcome the limitations of …

Recognizing and Preventing Exploits in Laravel
Syukra
Laravel is one of the most popular PHP frameworks in the world, especially among web developers because of its ease of use, good performance, and the security …

Google Hacking Database (GHDB): Uncovering Cyber Security and Techniques
Syukra
In this digital era, information can be easily found through search engines like Google. However, behind the common usage, there is a special technique known as …

Understanding Databases and Their Various Importance
Syukra
In the increasingly advanced digital world, data is one of the most valuable assets. A database is a system used to store, manage, and organize data …

Programming Logic Often Used on Online Gambling Websites
Syukra
In today’s digital era, the development of websites that provide online gambling and gaming services is increasingly rapid. Many aspects of programming …

Most Dangerous Ransomware Virus Types
Syukra
Ransomware is a type of malware that encrypts user data and demands a ransom to restore access to that data. Ransomware has become a serious cyber threat, with …
