New Post
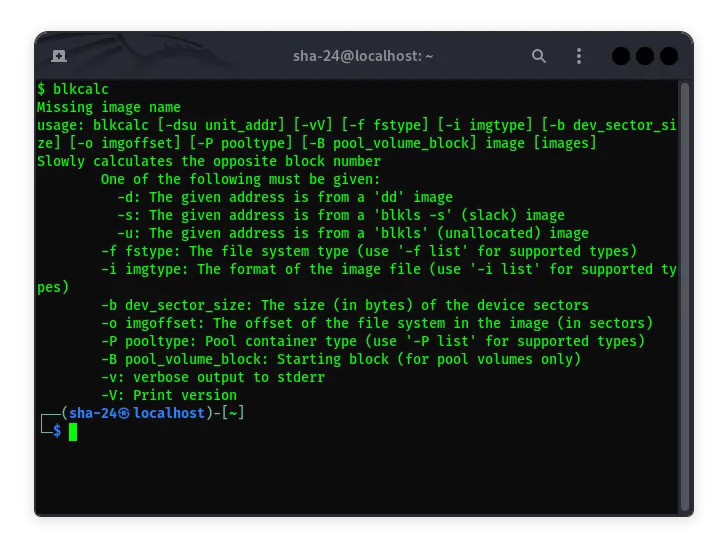
Getting to Know blkcalc in Kali Linux: A Complete Guide
Syukra
Kali Linux is a Linux-based operating system distribution specifically designed for digital forensics and security testing. One of the essential tools available …

What Is BleachBit in Kali Linux and How Does It Work?
Syukra
BleachBit is an open-source tool designed to clean up unnecessary files on the operating system. It is known for its ability to remove temporary files, caches, …

What is AppArmor in Kali Linux?
Syukra
AppArmor (Application Armor) is one of the security mechanisms used in the Linux operating system to limit application capabilities based on security profiles. …

How Adblock Works: The Technology Behind It Explained
Syukra
Adblock has become an essential tool for many internet users looking to improve their browsing experience. By blocking ads, Adblock helps speed up page load …

How to Use Binwalk on Kali Linux for Firmware Analysis
Syukra
Binwalk is one of the tools often used in the world of cybersecurity to perform firmware analysis. Binwalk is used to extract files contained in firmware, be it …

How to Use Bettercap Tools Kali Linux
Syukra
Bettercap is one of the powerful tools used to attack networks. This tool is often used by security professionals for penetration testing and by network …
