New Post
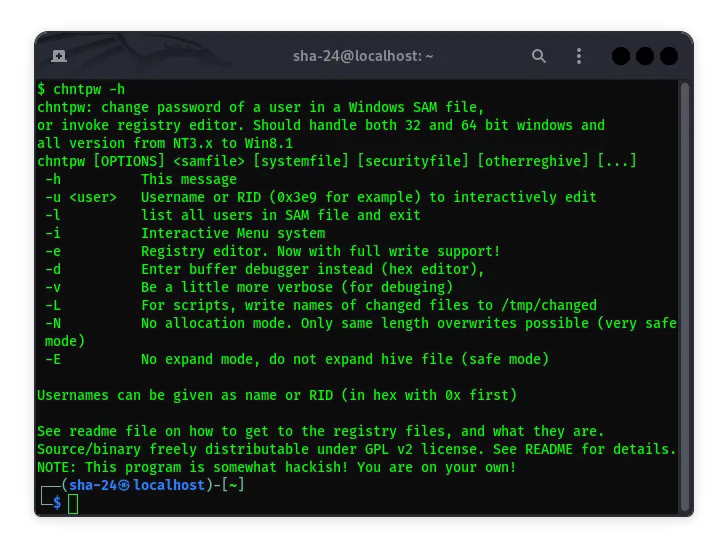
CHNTPW on Kali Linux: A Tool to Reset Windows Password
Syukra
CHNTPW (Change NT Password) is a very useful tool for system administrators and IT enthusiasts who need to reset or remove Windows account passwords. This tool …
Guide to Using CherryTree on Kali Linux
Syukra
CherryTree is a hierarchical note-taking application used by many cybersecurity professionals, including Kali Linux users. As a highly flexible tool, CherryTree …
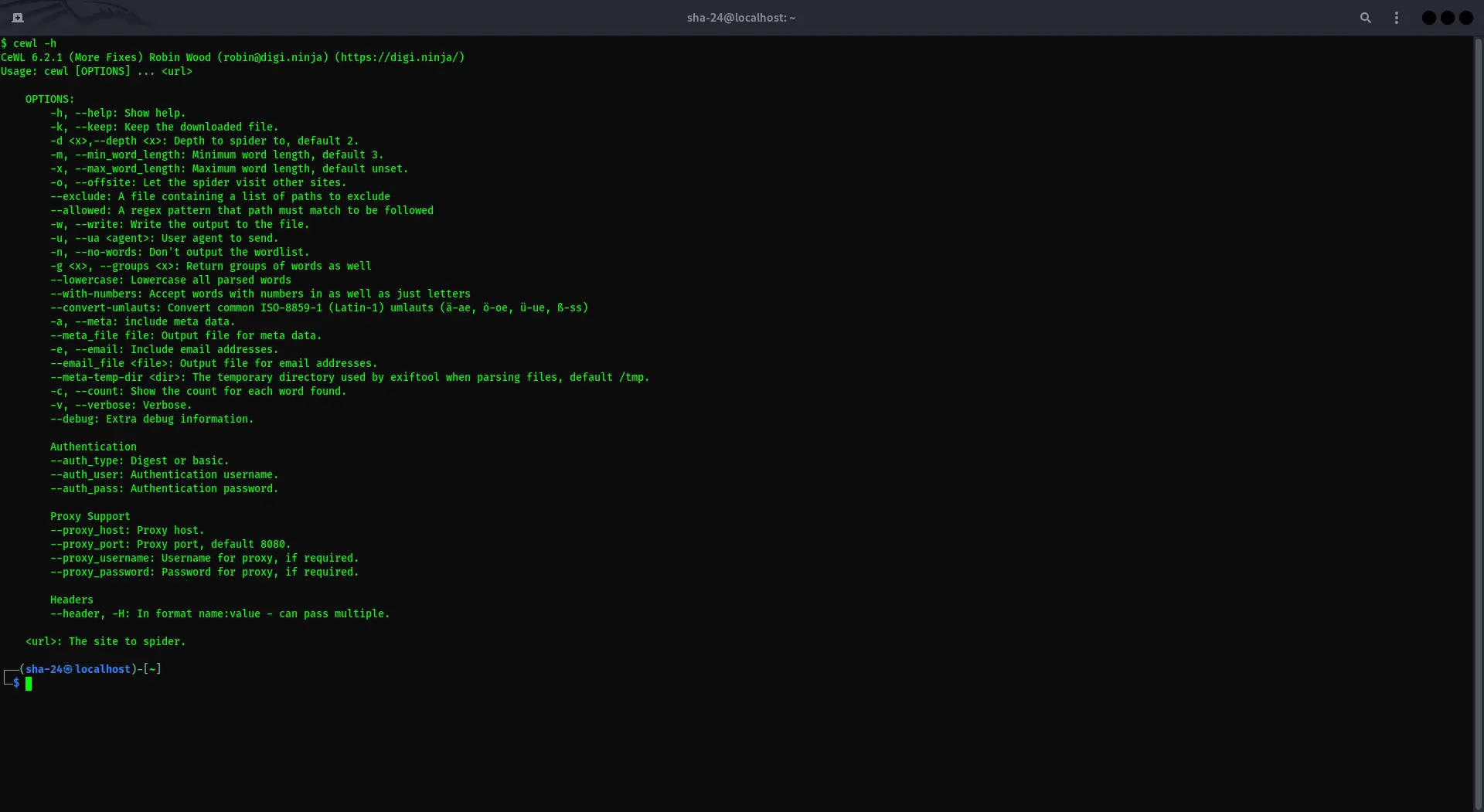
CEWL on Kali Linux: A Complete Guide to Using Custom Word List Generator
Syukra
Kali Linux is a popular Linux distribution designed specifically for pentesting and cybersecurity purposes. One of the tools available in this distribution is …
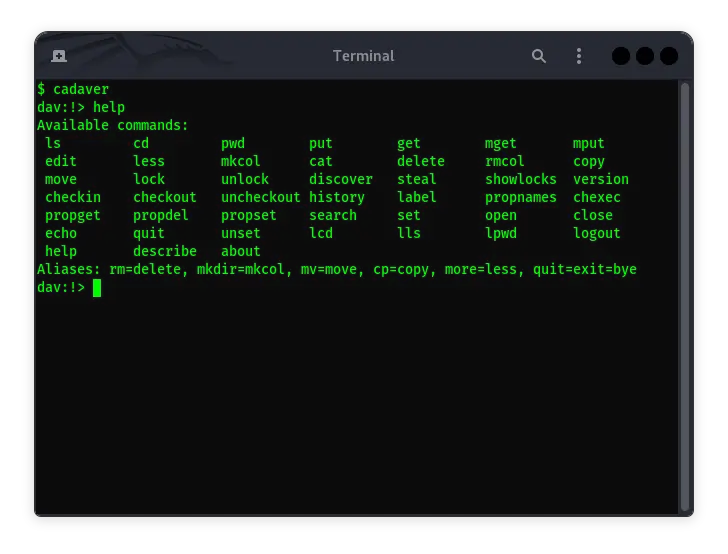
Cadaver in Kali Linux: Usage Guide and Features
Syukra
Cadaver is one of the command-line based tools used to interact with WebDAV (Web Distributed Authoring and Versioning) servers. WebDAV allows users to manage …
Burp Suite on Kali Linux: A Complete Guide to Web Application Security Testing
Syukra
Burp Suite is one of the most popular penetration testing tools for web applications. Developed by PortSwigger, it offers a range of features that allow …
Bully Cracking in Kali Linux: A Tool That Can Crack Wi-Fi Passwords
Syukra
Kali Linux has long been known as a specialized operating system for penetration testing and cybersecurity. One tool that often gets attention is Bully, an …
