New Post
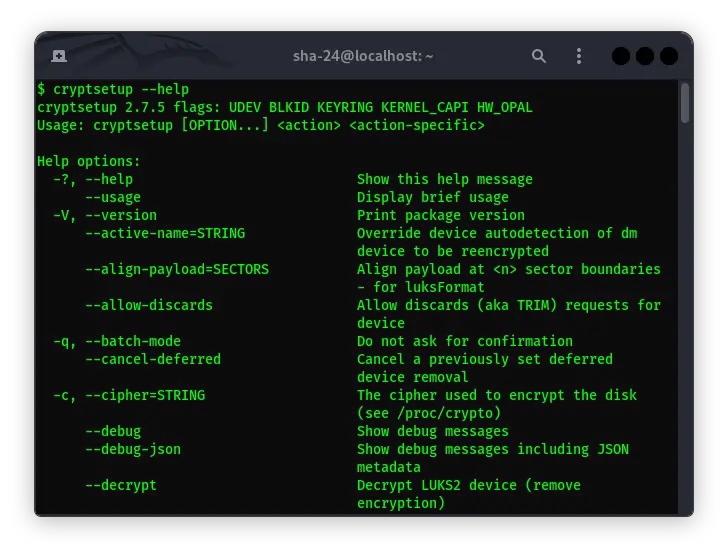
Complete Guide to Using Cryptsetup on Kali Linux
Syukra
Data security is becoming increasingly important in this digital era. One way to protect data is through encryption. Kali Linux, as one of the most widely used …
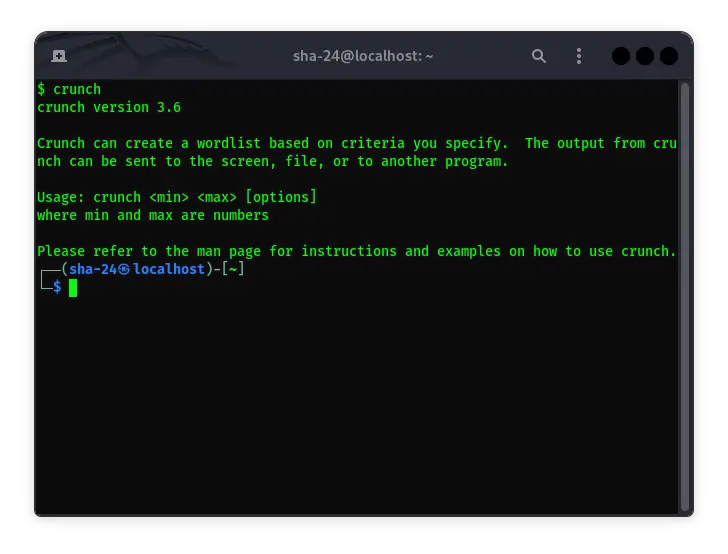
Crunch on Kali Linux: A Complete Guide to Using Password Generators
Syukra
Kali Linux is known as one of the best Linux distributions for penetration testing and ethical hacking purposes. One of the tools that is often used in this …
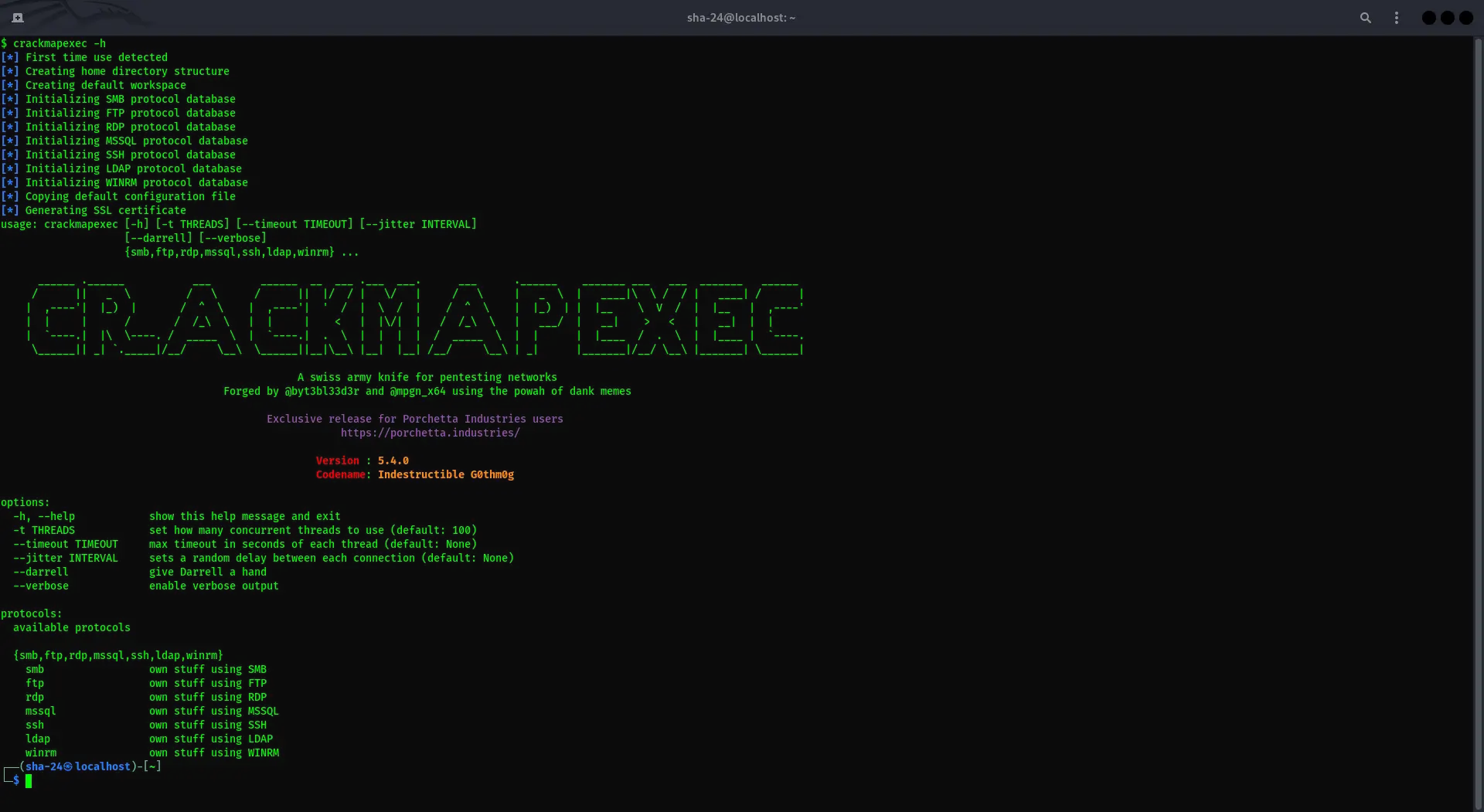
CrackMapExec on Kali Linux: Complete Guide
Syukra
CrackMapExec (CME) is a multi-purpose tool used by security professionals to audit Active Directory environments and test network security. CrackMapExec is …
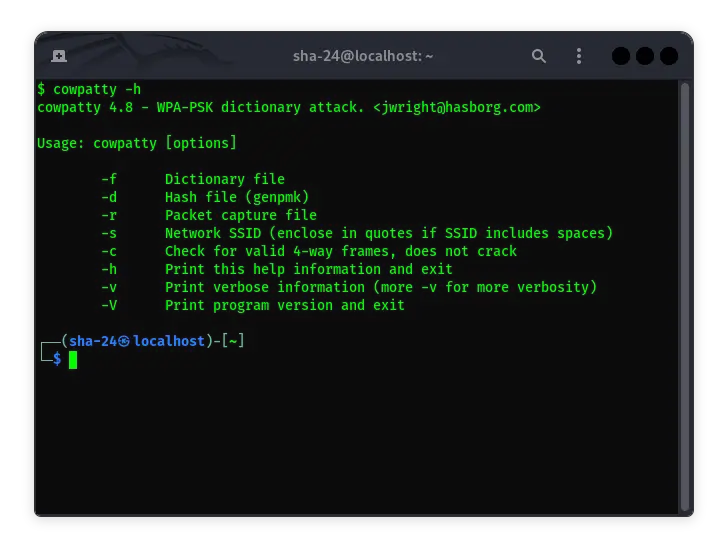
Getting to Know Cowpatty in Kali Linux
Syukra
Cowpatty is a tool designed to attack Wi-Fi networks that use the WPA-PSK (Wi-Fi Protected Access Pre-Shared Key) protocol. This tool can be used to crack WPA …
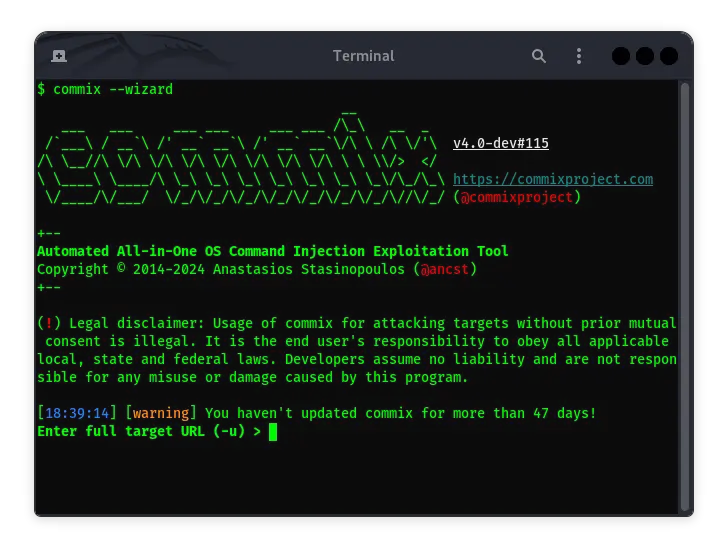
Commix on Kali Linux: The Complete Guide
Syukra
Commix (Command Injection Exploiter) is a very popular tool among pentesters and cybersecurity enthusiasts. It is designed to help detect and exploit command …
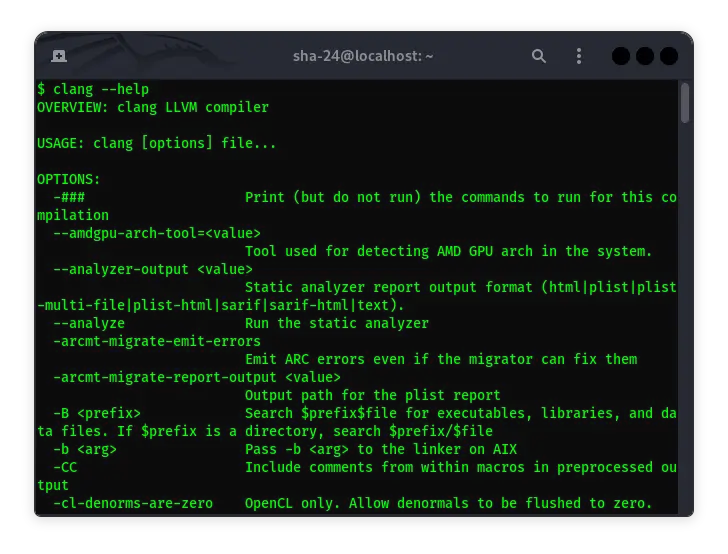
Clang and Clang++ in Kali Linux: A Complete Guide
Syukra
Kali Linux, a Linux distribution designed for cybersecurity professionals, is often used by security researchers and ethical hackers. One of the tools that can …
