New Post
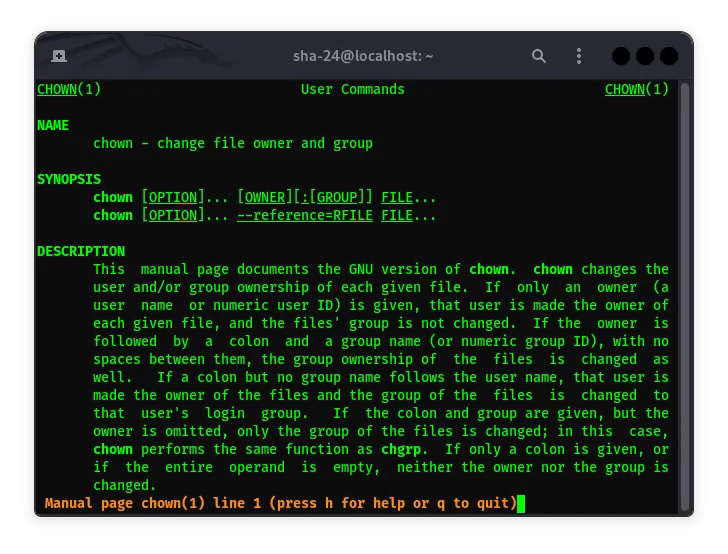
How to Use the Chown Command in Linux
Syukra
The chown command is one of the essential commands in Linux that is used to change the ownership of files and directories. This command allows you to control …
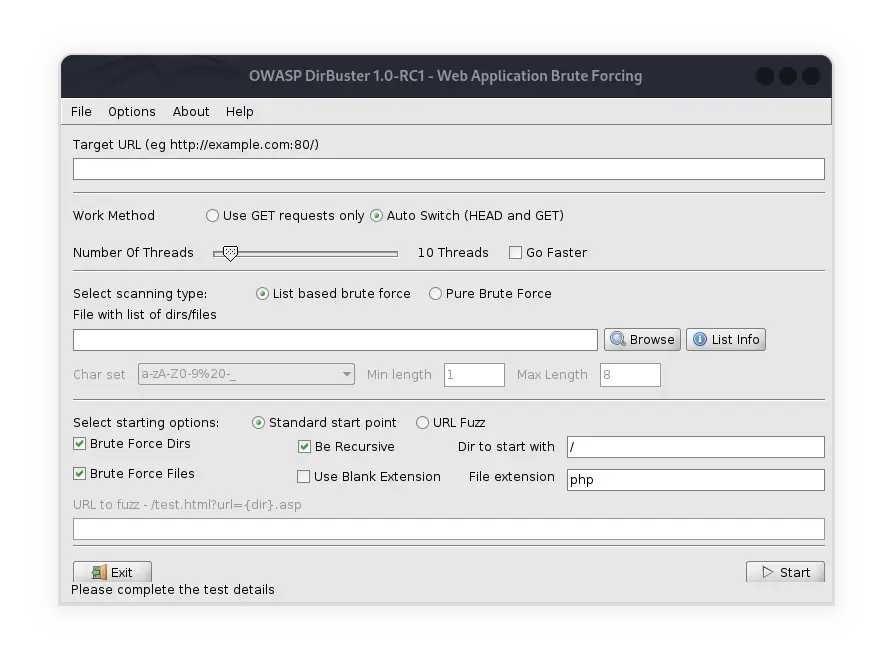
DirBuster on Kali Linux: The Complete Guide
Syukra
DirBuster is one of the most popular tools in the cybersecurity community, especially for those working in penetration testing and web application security …
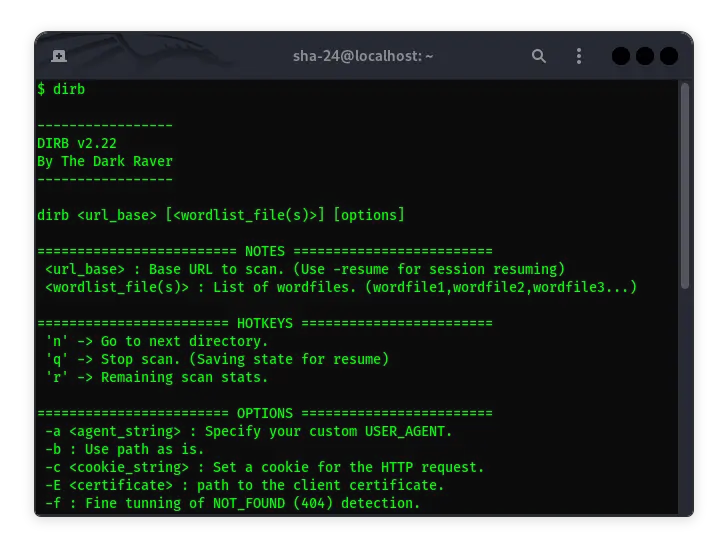
Dirb in Kali Linux: The Complete Guide
Syukra
Dirb is one of the essential tools in the world of cybersecurity, especially for web penetration testing. This tool is known for its ability to find hidden …
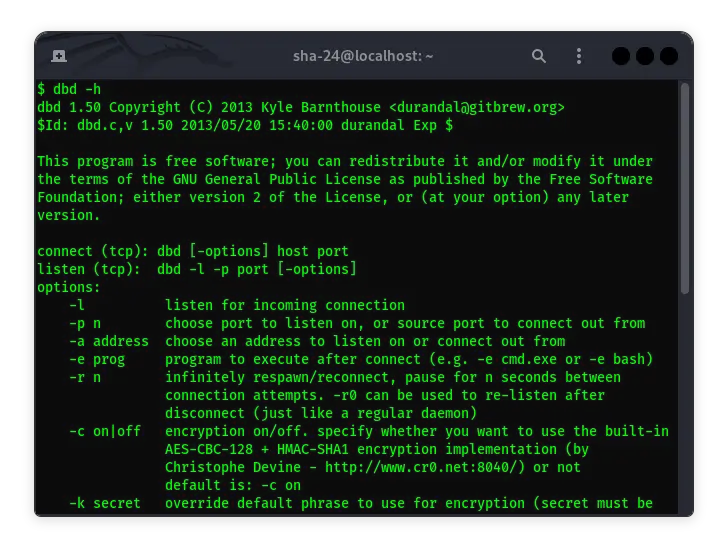
How to Use dbd Kali Linux
Syukra
Kali Linux, the preferred distribution for penetration testers and cybersecurity professionals, comes equipped with a myriad of tools designed to facilitate …
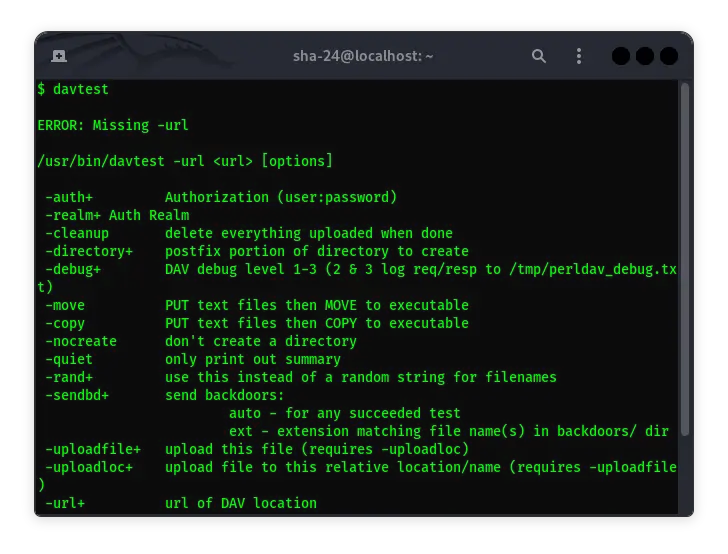
Complete Guide to Using Davtest on Kali Linux
Syukra
Davtest is a network security tool used to test WebDAV servers. WebDAV (Web Distributed Authoring and Versioning) is an extension of the HTTP protocol that …
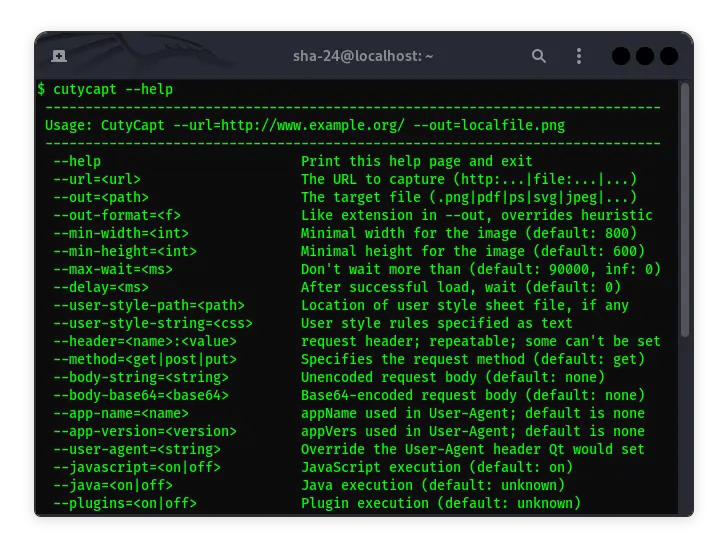
CutyCapt on Kali Linux: Complete Guide
Syukra
CutyCapt is a command-line screenshot tool that is very useful for taking screenshots of web pages in various formats, such as PNG, JPEG, SVG, PDF, and more. On …
