New Post
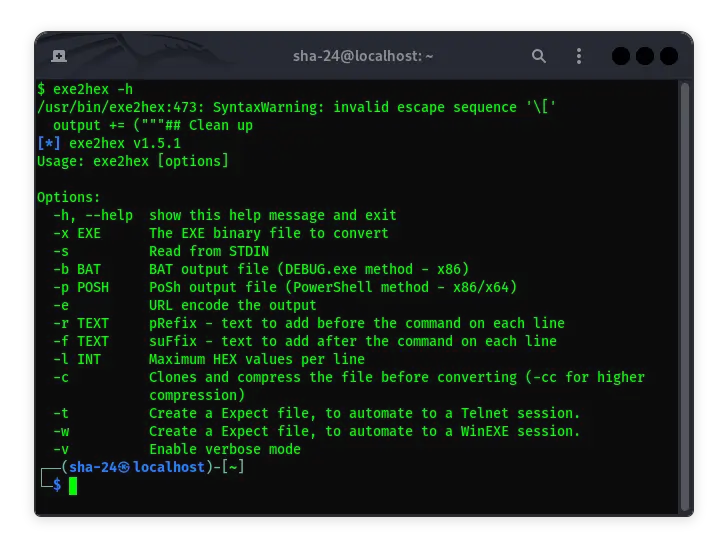
Complete Guide to Using exe2hex on Kali Linux
Syukra
In the world of cybersecurity, it is often necessary to process executable (.exe) files for various purposes, ranging from malware analysis to exploitation. One …
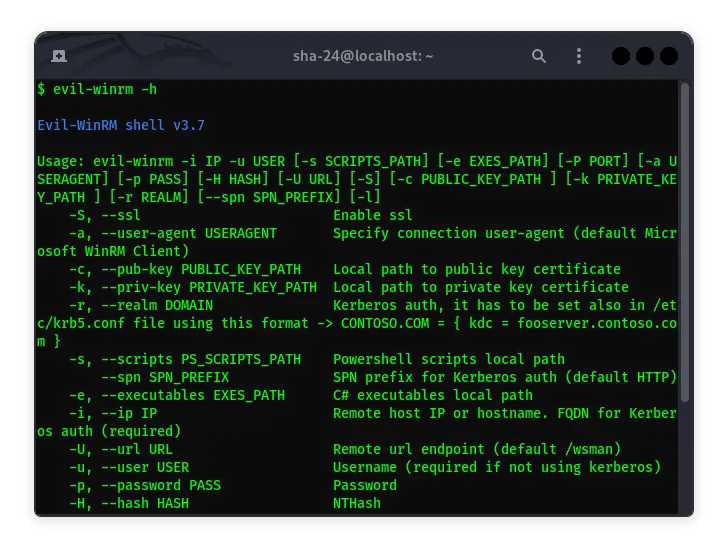
Complete Guide to Evil-WinRM on Kali Linux
Syukra
Evil-WinRM is a WinRM (Windows Remote Management) shell specifically designed for hacking and pentesting purposes. WinRM itself is an implementation of the …
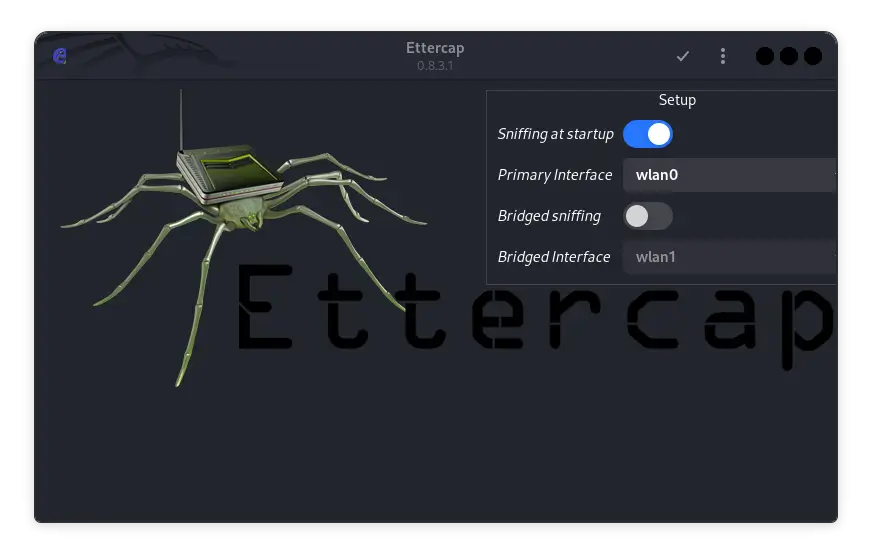
Ettercap on Kali Linux: Complete Guide
Syukra
Ettercap is a very popular tool in the cybersecurity community for performing man-in-the-middle (MITM) attacks. Developed to support various types of network …
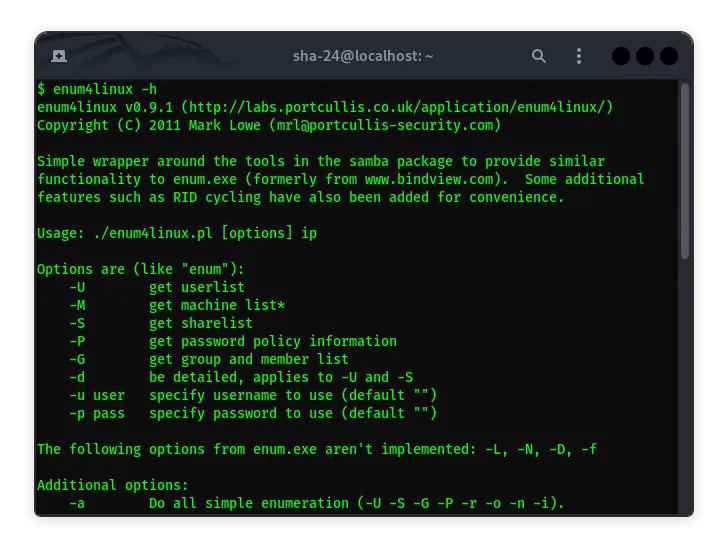
Enum4linux in Kali Linux: Complete Guide
Syukra
Enum4linux is a script-based tool used to enumerate information from Windows servers and Samba-based systems. This tool is very useful for information security …
Dsniff on Kali Linux: The Complete Guide
Syukra
Dsniff is one of the most popular network security tools and is often used by cybersecurity professionals and network administrators. This tool is designed to …
DNSChef on Kali Linux: Complete and Detailed Guide
Syukra
DNSChef is an open-source tool that works as a DNS proxy for performing DNS spoofing. This tool is very useful for security researchers, software developers, …
