New Post

The Complete Guide to Freelance Websites: How They Work, Benefits, and Tips for Success
Syukra
Freelance websites have become one of the best solutions for individuals who want to work flexibly and companies that need professional services without having …

Status Code Error: Complete Guide and Detailed Explanation
Syukra
In the world of web development, status codes are an important element in communication between a client (browser or application) and a server. Status codes are …
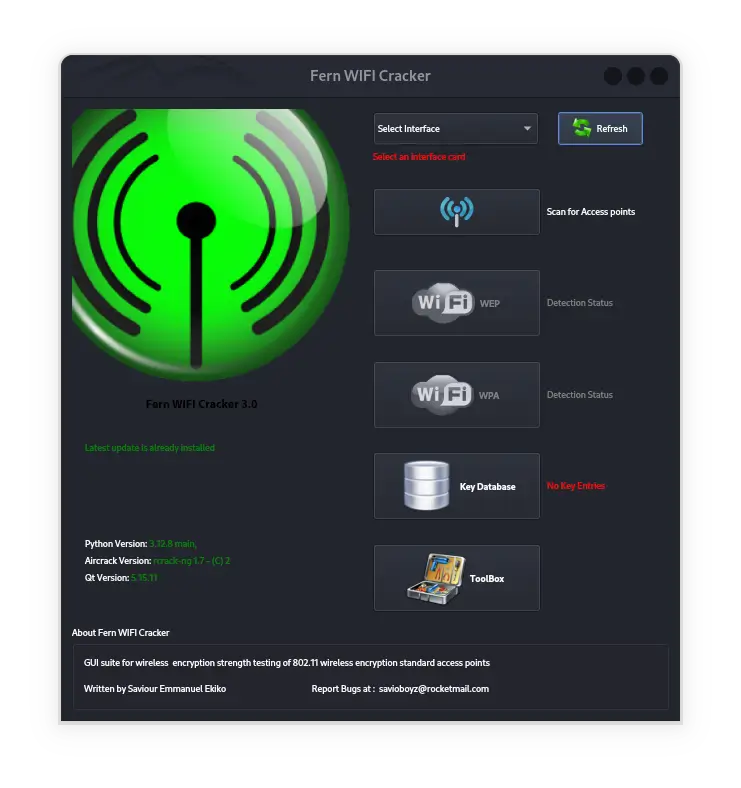
Getting to Know Fern Wifi Cracker on Kali Linux
Syukra
Fern Wifi Cracker is one of the popular tools available in the Kali Linux operating system. This tool is used to audit wireless (WiFi) networks and perform …
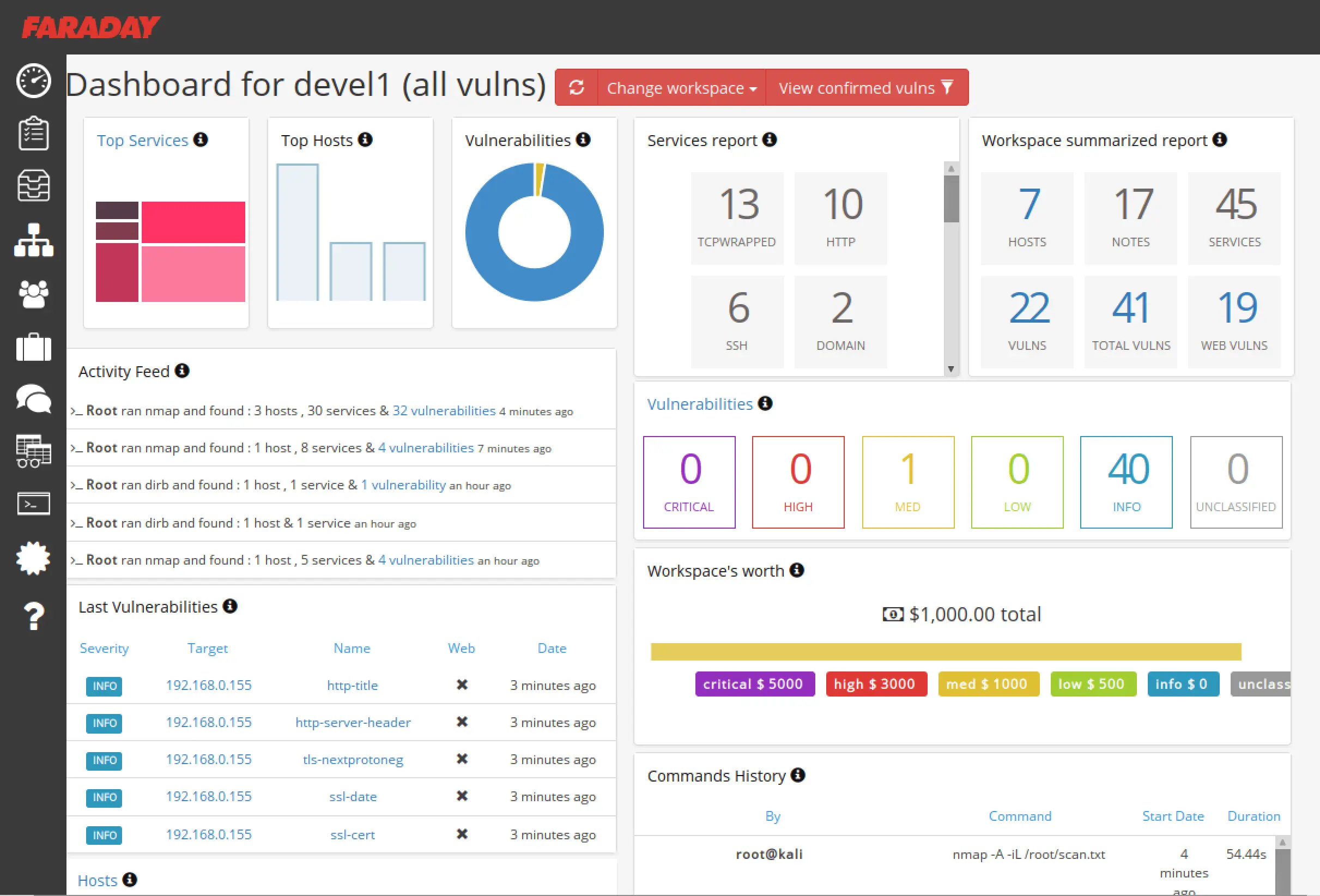
Faraday Kali Linux: The Complete Guide to Integrated Security Analysis
Syukra
Faraday is a collaborative security testing platform that is perfect for cybersecurity professionals, and when paired with Kali Linux, a popular distribution …
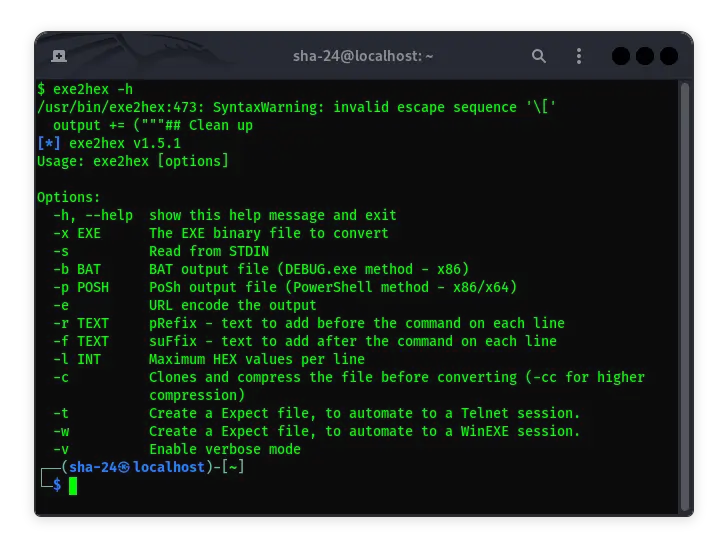
Complete Guide to Using exe2hex on Kali Linux
Syukra
In the world of cybersecurity, it is often necessary to process executable (.exe) files for various purposes, ranging from malware analysis to exploitation. One …
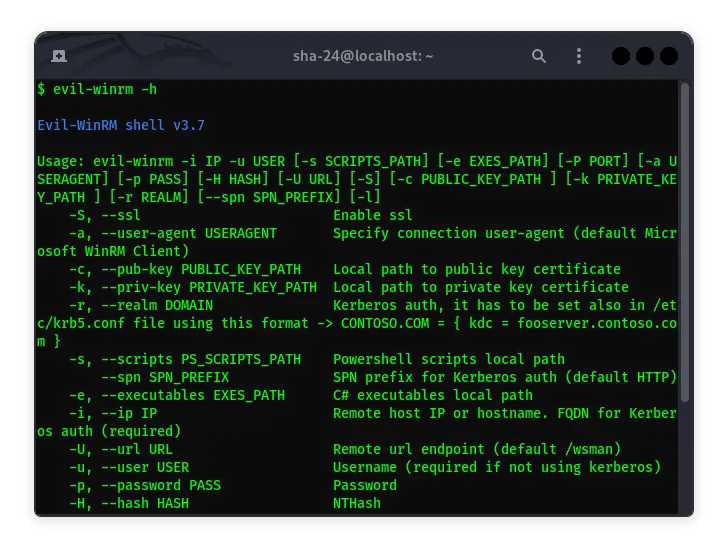
Complete Guide to Evil-WinRM on Kali Linux
Syukra
Evil-WinRM is a WinRM (Windows Remote Management) shell specifically designed for hacking and pentesting purposes. WinRM itself is an implementation of the …
