New Post

CVE-2024-30038: Full Analysis of Win32k Vulnerability and How to Fix It
Syukra
In May 2024, Microsoft released information about a new, fairly serious security vulnerability, namely CVE-2024-30038. This vulnerability was found in the …

CVE-2024-30085: Privilege Escalation Vulnerability in Windows Cloud Files Mini Filter Driver
Syukra
In 2024, a critical security vulnerability identified as CVE-2024-30085 was discovered in the Windows operating system. This vulnerability allows attackers to …

Download Oracle VirtualBox: Complete Installation and Configuration Guide
Syukra
Oracle VirtualBox is one of the most popular and widely used virtualization software worldwide. With VirtualBox, users can run various operating systems (OS) …

How to Resolve Error in Faraday: EXCEPTION of type 'Exception' occurred with message: Unknown error: <class 'Exception'> - Unknown error: <class 'TypeError'> - string indices must be integers, not 'str'
Syukra
Faraday is a collaborative penetration testing platform designed to help security teams manage and process test data more efficiently. Faraday allows pentesters …
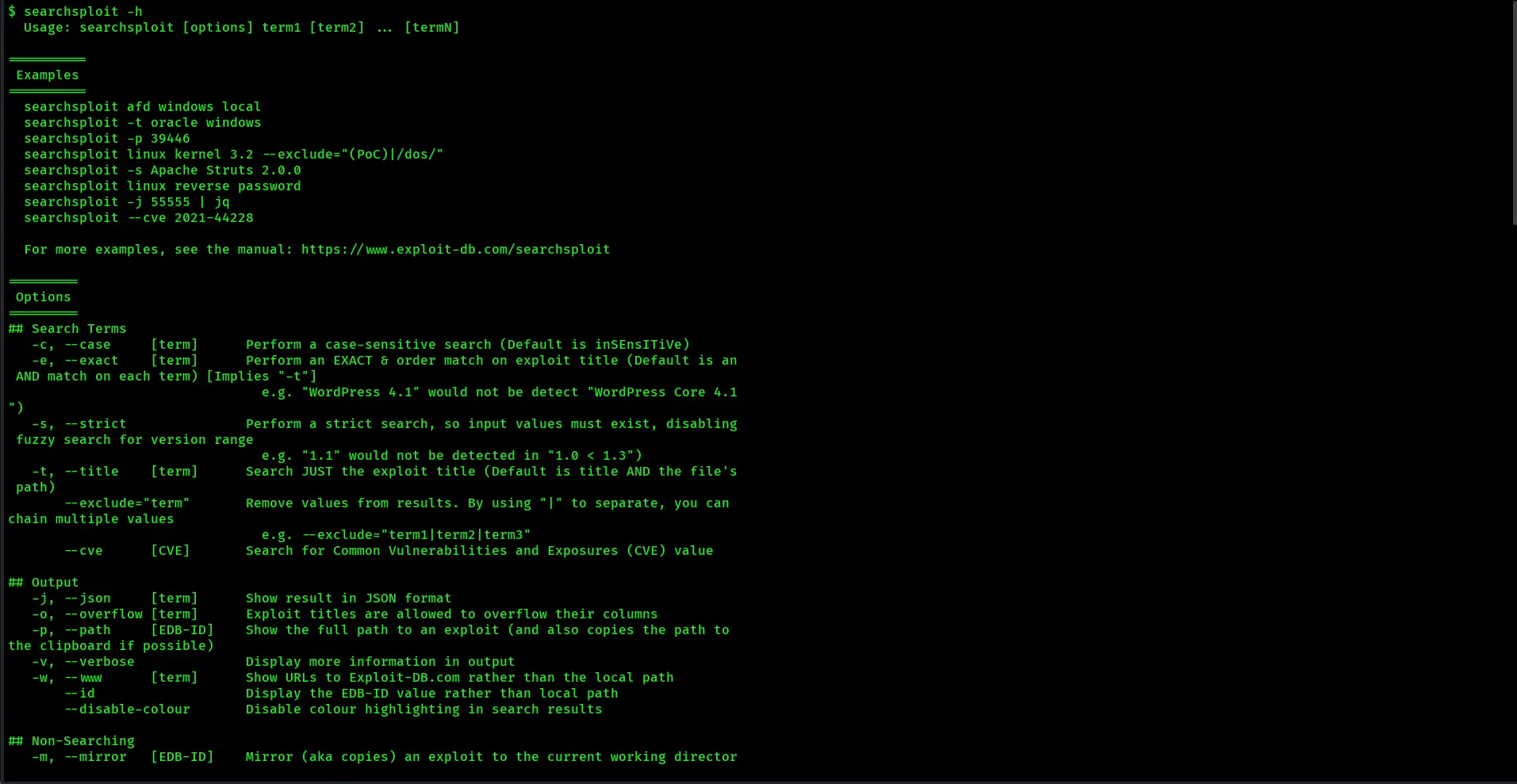
How to Use SearchSploit on Kali Linux: A Complete Guide for Beginners and Professionals
Syukra
SearchSploit is one of the most useful tools in the world of cybersecurity, especially for penetration testers and ethical hackers. This tool allows users to …

How to Use Skipfish on Kali Linux: Complete Guide for Beginners
Syukra
Skipfish is a web security scanning tool developed by Google. It is designed to automatically scan websites and provide reports on potential security …
